Encrypted and verifiable messages with JSON Web Tokens
You can use JWT as your message transport protocol. To sign and encrypt the messages you can use a technique known as nested JWTs, illustrated in Figure 4-8.
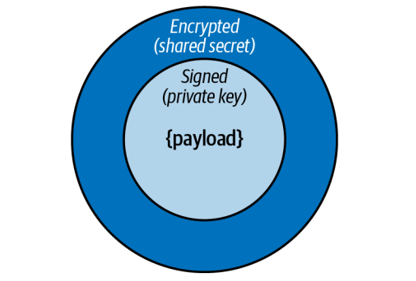
Figure 4-8. A nested JSON Web Token
The producer must first sign the message payload with the private key and then encrypt the signed message using a shared secret:
const payload = { data: { hello: “world” } };
const signedJWT = await new SignJWT(payload)
.setProtectedHeader({ alg: “ES256” })
.setIssuer(“urn:example:issuer”)
.setAudience(“urn:example:audience”)
.setExpirationTime(“2h”)
.sign(privateKey);
const encryptedJWT = await new EncryptJWT(signedJWT)
.setProtectedHeader({ alg: “dir”, cty: “JWT”, enc: “A256GCM” })
.encrypt(sharedSecret);
Public/private encryption key pairs and shared secrets should be generated separately from the runtime message production and stored in AWS Key Management Service (KMS) or AWS Secrets Manager. The keys and secrets can then be fetched at runtime to sign and encrypt the message.
Upon receipt of a message, the consumer must first verify the signature using the producer’s public key and then decrypt the payload using the shared secret:
const decryptedJWT = await DecryptJWT(encryptedJWT, sharedSecret); const decodedJWT = await VerifyJWT(decryptedJWT, publicKey);
// if verified, original payload available at decodedJWT.payload
Only the producer’s public key and the shared secret should be distributed to the message’s consumers. The private key should never be shared.
Built-in message verification for SNS
In addition to the approach outlined in the previous section, some AWS services, such as Amazon Simple Notification Service (SNS), are now beginning to support message signatures natively. SNS signs the messages delivered from your topic, ena‐ bling the subscribed HTTP endpoints to verify their authenticity.
Protecting Data
Data is the most valuable asset accumulated by any software application. This includes data personal to users of the application, data about third-party integrations with the application, and data about the application itself.
Cryptographic failure is the second of the OWASP Top 10 threats to web applications, after broken access control. This section examines the crucial role of data encryption in securing a serverless application and how you can encrypt your data as it moves through your system.
